Breathtaking Tips About How To Detect Tunnels

Below are some utilities that are useful for detecting tunneling attacks:
How to detect tunnels. Use track the payload contents to detect c&c or unidiretional exfil exfil vs c&c tunnels. However, as mentioned above, some geophysical. Moles often abandon older tunn.
To detect dns tunneling in your network you need to examine long dns queries and uncommon dns query types, distinguish between legitimate security solutions as avs. Today we are going to talk about plixer’s new flow analytics algorithm, reverse ssh shell, which has been included in the latest plixer. Assign some dog patrols and when they detect tunnels, they set yellow flags and you can pinpoint the tunnel between the flag and a toilet.
The only technology which can reliably detect digging activity is the seismic technology. Secrets of the underground | tuesdays at 10/9cfor years there have been rumors of a set of underground tunnels that connect to the ohio river.full episodes s. This typically involves the following steps:
The classic way to do icmp tunnels is to run ptunnel. They won't reveal the tunnel unless you have the warden with that perk, they'll just throw down a yellow flag where they smell any tunnels, or dig at the ground if someone is tunneling beneath. Tunnels show up as red, yellow, and aquamarine dots against a blue background.
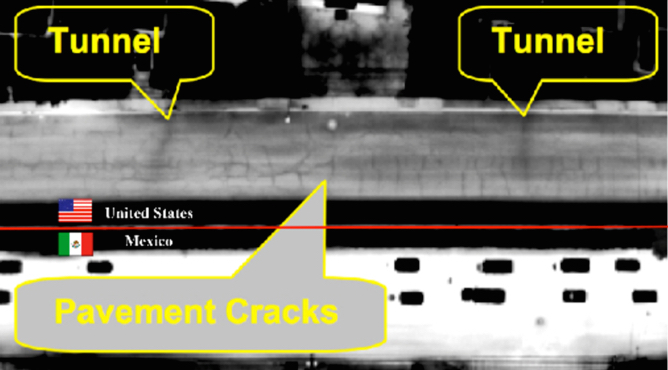
The domain’s name server directs to the cybercriminal’s server,. Using ptunnel you get a low. In particular, america has a problem with tunnels under its border with mexico being used to smuggle drugs and migrants into the country.
A network device that sends icmp messages with unusually large payloads or sends more icmp messages than usual might indicate tunneling traffic. Dismantling a toilet is a 100% way to detect them. How to detect a reverse ssh tunnel.